Passwords – “can’t stand them, can’t live without them.” We must access many computer resources every day and have to rely on passwords to verify we are who we say we are. I can’t count the number of times people ask me about what constitutes a good password. Therefore, I thought it might be appropriate to discuss passwords. Before proceeding, if you have the ability to utilize two factor authentication, do so. From a security perspective, we have three methods of confirming our identity:
- who we are (fingerprints, iris, ears, voice prints, DNA, and so forth). If these are ever hacked or able to be reproduced, you have a significant problem. For example, it is very difficult to change your fingerprints.
- what we know (this is where passwords come into play). We know a given value (a word or phrase) and use this to confirm our identity.
- what we have (this is where two factor authentication comes in to play). For example, if we enable two factor authentication for a social media site, we enter a password and then receive a text value on our phone. We must then enter that unique value within a short time frame. Failure to do so means our access fails (even if the password was valid). If you are reading this and want to employ 2 factor authentication, there are several solutions. One is WikID.
So, what constitutes a good password?
There are a several factors which we need to consider regarding the above question.
First, a good password is only used to access a single web site (or application). It should not be used for any other site or app. This insures that if your password is compromised on the single site, the exposure is only to that site.
Second, the password should be long and complex. When in doubt, length wins. If you have any passwords which are 9 characters or less, change them. Do it now. Stop reading and just do it. Yes, I am serious. Tools and data stores called rainbow tables exist which allow any string of characters (upper case, lower case, numbers, special characters in any combination) to be cracked in seconds.
Next, the password should not be easy to guess. This also applies to those pesky answers to password reset questions. Yet, so much of our information is leaking via social media that it is difficult to make these difficult to guess.
Ok, knowing the above, which of the following is a more secure password?
dog1234567890
J&3zQ#91hH!
Short answer – the first one (it is longer). Length wins over complexity. However, if both passwords were the same length, select the more complex one.
Next question – how do I remember unique passwords for every site I visit? Yes, you really should use a separate password for every site. Short answer – use a password vault. There are many solutions. I am not endorsing any of these. Examples include Keepass (you can even run this as a portable app using a USB drive), LastPass, Dashlane and many others. PCMag has a good side by side comparison of the best choices in 2015. I recommend picking one which works across devices (so you can access your credentials from your smartphone, tablet, or desktop).
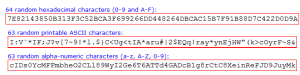
For those who want long and complex password (and plan to store them in a password vault), I recommend Gibson Research (perfect passwords). I have included a screen snippet below showing the types of passwords this tool generates. Of course, these can not be memorized – hence the need for a password vault. Click on the image below to see a larger version.
If you absolutely refuse to use a password vault, may I recommend some of the following approaches…
Use a passphrase (yes, you can often include spaces in your password these days).
One example would be – “This is my really long and complex password for the named site!” – Yes, include the quotation marks and spaces. Replace named site with the name of the site you are visiting. Of course, anyone who cracks this password will be able to figure out what you used on other sites. If you want to make it a little more difficult to guess, replace the name of the site with a 2 character code [representing the length of the site name and the first letter of the site – for example 6a for amazon.com – 6 characters starting with the letter “a”). Keep in mind some sites limit the length of your password. You would have to modify the phrase accordingly. Sadly, a few years ago, I did business with a bank which limited my password to 6 characters or less. As you may suspect, I did the only logical thing – I stopped using that bank. Yes, I tried to explain to their customer service they were asking for problems. No, I won’t name the bank.
One thing to consider – use a completely different password for your email. Note that many sites include a password reset capability. It relies on your email. If someone hacks your email, they can then reset all your other passwords.
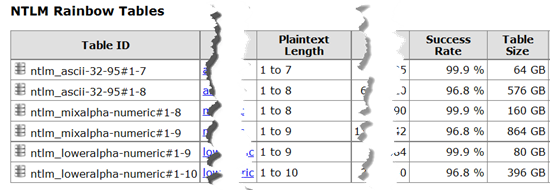
For those who have read this far and don’t believe that rainbow tables actually exist, I provide the following sanitized screen capture (yes this is a real website – if I don’t want to spend the time downloading, I can purchase any of these tables as a set of DVDs for less than $10). I chose NTLM format, but they exist for nearly type of encryption that exists.
Note the length of the password is up to 9 characters (again, if you use a password of 9 characters or less, stop reading and change it – length wins over complexity). Note the success rate in all cases is over 95% (do you really think your password is that complex to fit in the last 5%)? Note that these files are also huge (864 GB, for example). This is why length wins over complexity (as we add another character, the size of the rainbow table grows almost exponentially).
Ok, I get it, but what about those security phrases to help reset our passwords. For example one of my favorites – “What was the name of your high school?” I could probably figure that out for almost anyone these days (especially if they have a social media presence). Yes, you could lie, but then you have to remember the false information. Better – add something to your answer (either at the beginning or end) that would be known only to you. If the real answer is “Jefferson High” you would use “Jefferson High 42” instead. Mother’s maiden name “DuBois 42” – you just have to be consistent throughout.
I much prefer those sites which allow you to set your own question and response. In those cases, I recommend something along the lines of the following.
Question – Why am I trying to hack this person’s password?
Answer – I need to speak to your security team.
What hacker in their right mind would ask such a question or use the answer above? No, I don’t use this phrase, but I have something equally improbable for most hackers to ask.
Obviously, there is a lot more to be said about passwords. For now,
- make certain you use two factor authentication if it is available.
- Use a password vault with long and complex passwords.
- Use a different one for each site.
Make it painful for someone to try to learn your password. Most times the individual will stop trying and go elsewhere. That is about the best we can expect these days.
I am curious if you found this information helpful. As always, I look forward to your comments.